A blessedly quick objective this one! Quite why the ESXi Configuration Guide is listed in the blueprint is anyone’s idea as ESXi doesn’t contain a firewall! The blueprint also lists vicfg-firewall which is a typo – they mean esxcfg-firewall, as vicfg-firewall doesn’t exist!
Knowledge
- Identify vicfg-firewall commands
- Explain the three firewall security levels
- Identify ESX firewall architecture with/without vCenter Server
Skills and Abilities
- Enable/Disable pre?configured services
- Configure service behavior automation
- Open/Close ports in the firewall
- Create a custom service
- Set firewall security level
Firewall architecture
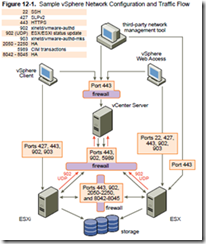
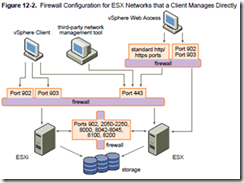
The ESX Configuration Guide talks very generally about where to put firewalls to protect traffic. In reality I can’t see much difference in architecture whether you have a vCenter server or not. These two diagrams are from the ESX Configuration Guide – minimal differences!
The firewall is ESX only (there’s no ESXi firewall as no service console).
Firewall security levels
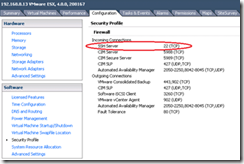
Three firewall security levels (high is default);
- High (outbound blocked, limited inbound allowed (902, 443,22,123 and a few other including ICMP).
- Medium (outbound allowed, inbound blocked apart from allowed services)
- Off
Continue reading VCAP-DCA Study notes 7.2– Configure and Maintain the ESX Firewall