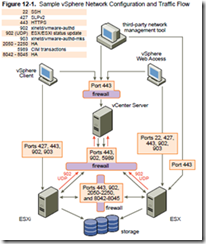
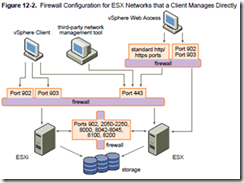
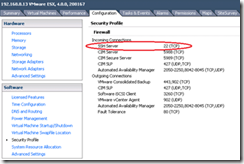
vShield Zones is basically a firewall framework to protect your VMs without requiring external or hardware based firewalls. It requires Advanced or higher licencing. For study I’d suggest going through Eric Siebert’s blogposts (part one, two, and three) to start with (they cover real world issues) and then getting stuck into the official docs – they cover everything on the blueprint. There’s quite a bit to learn making this is one of the larger objectives on the VCAP-DCA blueprint.
NOTE: vShield Zones is NOT the same as vShield App, Edge, and Endpoint so make sure you download the right version. The VCAP-DCA exam only covers v1.0 of vShield Zones (not the most recent v4.1) and doesn’t cover the more feature rich vShield App Suite. See VMware’s product page for more details.
Knowledge
- Identify vShield Zones components
- Identify the four CLI command modes
Skills and Abilities
- Configure vShield Zones
- Backup and restore vShield Manager Data
- Backup CLI Configuration
- Create/Delete Layer 2/3/4 firewall rules using VM Wall
- Install/Uninstall a vShield manually and from template
- Configure vShield Manager plug?in capability
- Configure VM Flow charts
- Update vShield Zones
- Add/Edit/Delete User Accounts
- Assign rights to a user
- Add/Delete Application?Port Pair mapping
- Execute/Schedule Execution of virtual machine discovery
- Utilize vShield Zones CLI commands to configure and monitor vShield Zones
- Analyze traffic using VM Flow to determine root cause of network related issues
Installing vShield Zones
Deployed as an appliance with two components;
- Setup the vShield Manager appliance
- Deploy the vShield Manager from OVF
- Create a port group on the vSwitch which hosts your VM traffic, named vsmgmt and amend the vNIC on the vShield Manager VM to use this network.
- Power up the VM, login with ‘admin’ and ‘default’, then run ‘setup’ to configure the server.
- Allocate IP details
- Upgrade VMtools (you can use the ‘Automatic’ option – being Linux based no reboot is required)
- Initial install of the vShield Agent
- Deploy from OVF and then convert to a template. This simply gets the agent ready for deployment.
If you’re wondering whether VMtools make a significant difference to this customised Linux appliance see (the pointless) VMwareKB1011501! You can also find out what’s new in vShield Zones 1.0 Update 1.